A leading Indian OEM for CryptoBind® Network Security Module (HSM) introduces a high performance hardware based transaction security solution for cloud data centers, enterprise, government organizations & ecommerce applications.
Overview
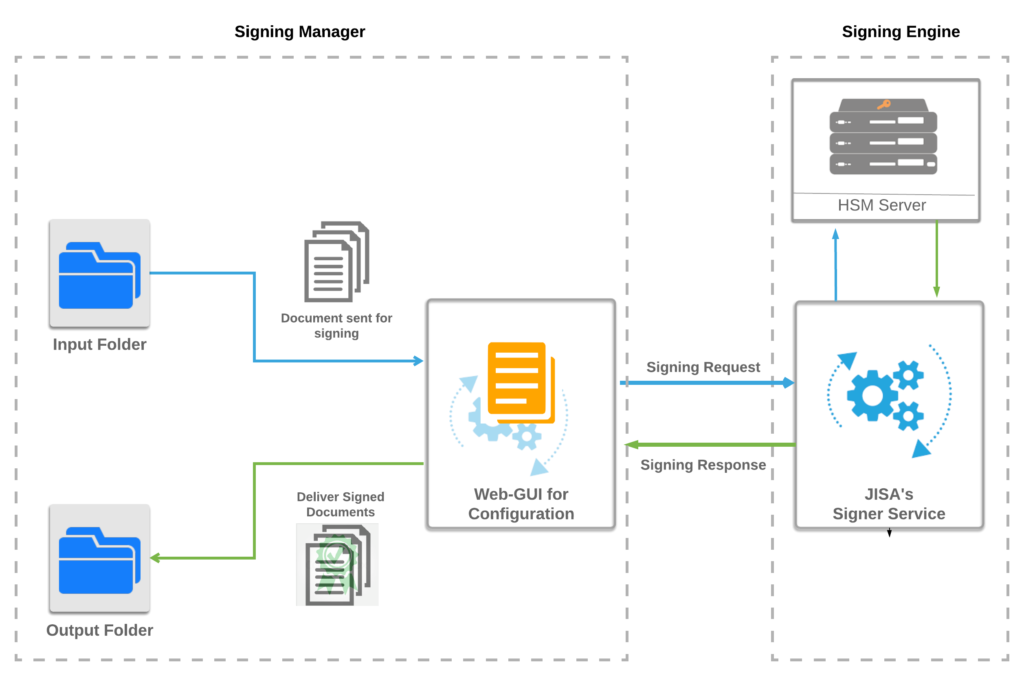
JISA launches CryptoBind® Network Appliance HSM (Hardware Security Module) powered by LiquidSecurity ,HSM family provides a FIPS 140-2 level 3 certified solution that provides elastic and centralized key management and key operation functionality. With upto 1000 partitioned HSMs in a single physical HSM, 100,000 key store independent of key size, 35,000 2048b RSA ops/sec and chaining of up to 20 Appliances, CNN35XX family provides a solution that addresses requirements from few hundred RSA ops/sec or few key stores to 700K RSA ops/sec or 1M key store and everything in-between.
CryptoBind® HSM also comes with EAL4+ Compliant Cryptographic Boundary which makes CryptoBind® HSM EAL4+ Compliant to meet Common Criteria requirements.
This product family, available as a network HSM appliance, offers a no compromise cost efficient solution that addresses the stringent security requirements of SaaS applications, ecommerce payment systems and Enterprise, Banking and Government security applications especially as they migrate to the Public or Private cloud.
Major applications for this product family include Key Management as-a-Service, Database as-a-Service, Crypto as-a-service, Secure DNS, SaaS Applications and Virtual Private Clouds in the Public Cloud.
Key Features
Below listed are some key feature of CryptoBind® Network Appliance HSM (Hardware Security Module)
Capabilities
- 35K 2048b RSA ops/sec
- 10G Bulk crypto / sec
- 11K ECC ops/sec
- 100K any size key store in crypto memory
- Up to 1000 Partitions per appliance
- Two Factor Authentication
- Extensive key management
Power Supply
- 2 x 1U 550W/300W 80+certified Hot Swappable Power Supply
- Power Efficiency : 94%
- Output and Input :550W/300W with Input 100 – 240Vac
- AC Input Freq. : 50-60Hz
- Power Distributor:
- O/P: 12V/75A
- +5V Max: 30A
- +3.3V Max: 24A
- -12V Max: 0.6A
- Power supply terminations for different PCBs is uniform.
Division of Roles
- Appliance admin: Create, enable/disable partitions but no access to keys in FIPS boundary
- Partition admin: Create users per partition
- Partition Users: Create, import keys and use them
Out of the Box solution
- Cryptographic APIs such as PKCS11, Java JCA, OpenSSL
- Health checks, Audit logs
Network Interface
- Dual network Interface
- option of 1GbE or 10 GbE
Supported OS
- Windows and Linux
Operating Environment / Compliance
- Operating temperature: +10°C to +50°C (+50°F to +122°F)
- Storage temperature: -10°C to +55°C (+14°F to +131°F)
- Relative humidity: 10% to 95% non-condensing
- RoHS Compliant
- Complies with FCC standard for Electromagnetic compatibility (EMC)
Physical specifications network appliance
- Available as 1U and 2U appliance
RSA
- KeyGen: 2048, 3072 and 4096-bit
- PKCS #1 1.5 SigGen: 2048 and 4096-bit (SHA-224, 256, 384, 512)
- PKCS #1 1.5 SigVer: 1024, 2048 and 4096-bit (SHA-1, 224, 256, 384,512)
DSA
- PQG Gen: 2048 and 3072-bit (SHA-256)
- PQG Ver: 1024-bit (SHA-1); 2048 and 3072-bit (SHA-256)
- Sig Gen: 2048-bit (SHA-224, -256, -384, -512)
- SigVer: 1024, 2048 and 3072-bit (SHA-1, 224, -256, -384, 512)
ECC
- ECC CDH: P-224 and P-256 with SHA-256,P-384 and P-521 with SHA-512
HASH
- SHA: 1, 224, 256, 384, and 512 , MD5
AES
- ECB mode: Encrypt/Decrypt; 128, 192 and 256-bit
- CBC mode: Encrypt/Decrypt; 128, 192 and 256-bit
- GCM mode: Encrypt/Decrypt; 128, 192 and 256-bit
Triple-DES
- TECB mode; 3-key
- TCBC mode; 3-key
RNG
- Hardware Random Number Generator (NDRNG)
Other Supported Algorithms
- PBE, RC2, RC4, RC5, Diffie-HelliMan
ECDSA
- PKG: P-224, P-256, P-384, P-521, K-233, K-283, K-409, K571,
- B-233, B-283, B-409, and B-571
- PKV: All P, K and B curves
- Sig Gen: P-224, P-256, P-384, P-521, K-233, K-283, K-409,
- K-571, B-233, B-283, B-409, and B-571 (SHA-224, -256, –
- 384, -512)
- SigVer: All P, K and B curves (SHA-1, 224, -256, -384, -512)