
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed.
What is Code Signing Solution?
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. Code signing confirms the authenticity and originality of executables and scripts. It assures this information is valid and establishes the legitimacy of the author. Code signing process employs the use of a cryptographic hash to validate authenticity and integrity.
The most common use of code signing is to provide security when deploying; in some programming languages, it can also be used to help prevent namespace conflicts. Almost every code signing implementation will provide some sort of digital signature mechanism to verify the identity of the author or build system, and a checksum to verify that the object has not been modified. It can also be used to provide versioning information about an object or to store other Meta data about an object.
Why Code Signing is needed?
Today internet is the primary medium through which software is distributed, accessed and used. The worldwide use of this medium has also introduced risk factors. Hackers and cyber criminals may obtain secured executable files and insert malware into it. As a result any user downloading and accessing this file would fall victim to the malware.
Because of the potential damage that an executable or script can cause to a computer system, it is important that users be able to trust code published on the Internet. Code signing identifies that the software or application is coming from a specific source. It also ensures that a piece of code is not altered and it is trustworthy. Users are assured who they are downloading software from.
Benefits of Code Signing
Weakness of Code Signing
How CryptoBind Helps to overcome Weakness of Code Signing
The result is assurance that code signing credentials are protected from unauthorized internal or external use by leveraging a solution that enables development and InfoSec teams to work together more efficiently.
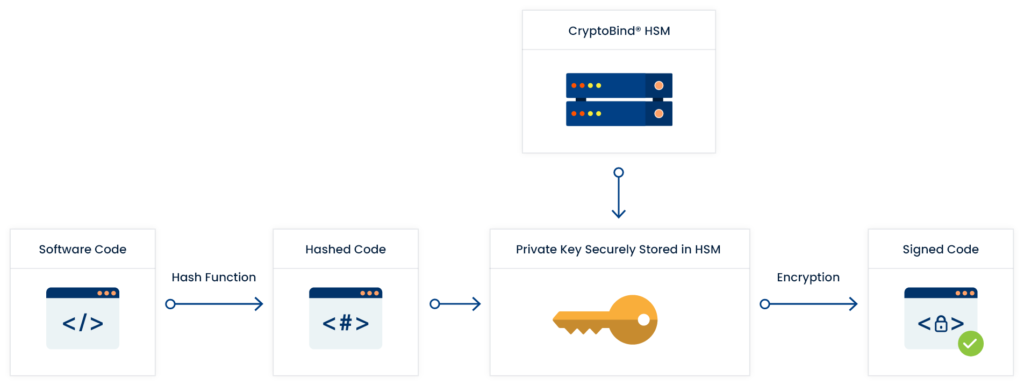
Features
Protect your keys
Protect sensitive code signing private keys in highly secure, flexible Hardware Security Module (HSM)
Attacks Prevention
Define policy-based access controls and workflows to prevent unauthorized signing
Audit everything
Gain visibility into all code signing keys and actions from a single console.
Easy and Secure Access
Make it easy for developers to sign code fast without handling sensitive keys
Move faster
Simplify and streamline code signing processes for your teams. Eliminate manual bottlenecks.
One platform, any team
Enable multiple development teams to sign code remotely via API, console, or remote utility
