
Data Security Server provides built-in HSM with encryption and tokenization solutions.
Overview
JISA launches Data Security Module by JISA powered by LiquidSecurity HSM (Marvell), this family provides a built-in FIPS 140-2 level 3 boundary for elastic and centralized key management and key operation functionality.
Data Security Module enable advanced format-preserving encryption, secure Stateless tokenization, and stateless key management to protect enterprise applications, data processing infrastructure, Data Encryption API etc.
Data Security Module provides built-in HSM with encryption and tokenization solutions. It enables organisations to neutralize the data breach impact for data at rest, in motion and in use by de-identifying sensitive information. Data Security Module solves the industry’s biggest challenge by simplifying data protection across complex legacy and modern IT.
Tokenisation
Tokenisation is the process of replacing sensitive data with unique identification symbols that retain all the essential information about the data without compromising its security.
JISA DSM comes with built-in Tokenisation with Dynamic Data Masking. Easy to implement format-preserving tokenization to protect sensitive fields in databases and policy-based dynamic data masking for display security.
Encryption
Application Encryption. Streamlines the process of adding NIST-standard AES encryption and format-preserving encryption (FPE) into existing applications. Offers standards based APIs that can be used to perform high-performance cryptographic and key management operations.
Types of data to protect can include:
- Credit card and other payment card numbers
- Names – surnames, first names, street names, suburbs
- Bank account numbers, Tax File Numbers,
- Phone numbers – mobiles and landlines
- Post codes and ZIP codes
- Identification numbers – driver’s license and passport numbers
- Dates – birth dates, join dates
- Currency amounts – salaries, bank account amounts, transaction amounts
- Social security, national security and Medicare account numbers
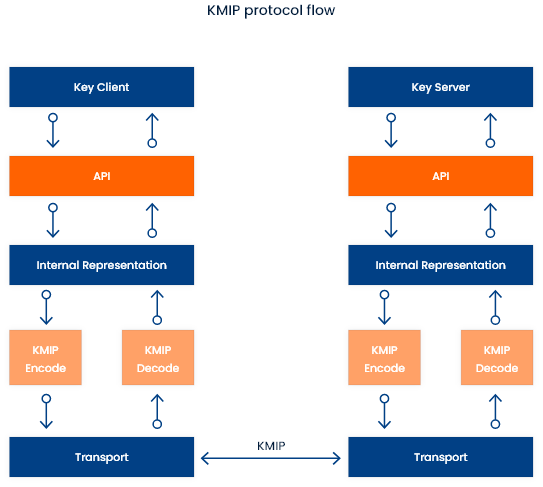
KMIP
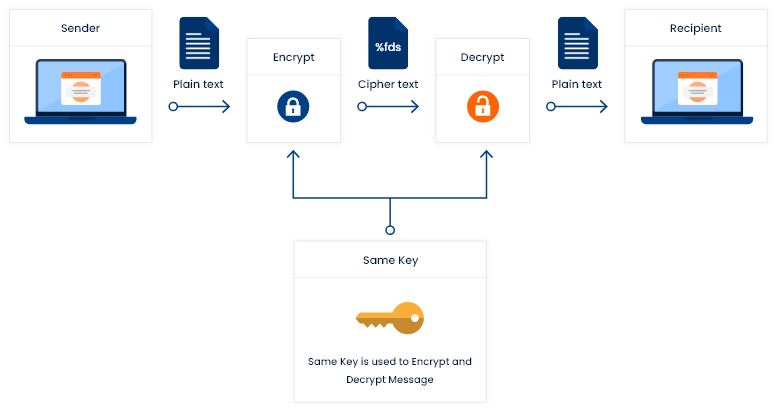
The Key Management Interoperability Protocol (KMIP) is an extensible communication protocol that defines message formats for the manipulation of cryptographic keys on a key management server. This facilitates data encryption by simplifying encryption key management. Keys may be created on a server and then retrieved, possibly wrapped by other keys. Both symmetric and asymmetric keys are supported, including the ability to sign certificates. KMIP also allows for clients to ask a server to encrypt or decrypt data, without needing direct access to the key.
A KMIP server stores and controls Managed Objects such as symmetric and asymmetric keys, certificates, and user defined objects. Clients then use the protocol to access these objects subject to a security model that is implemented by the servers. Operations are provided to create, locate, retrieve and update managed objects.
Data in Transit
Data in transit, or data in motion, is data actively moving from one location to another such as across the internet or through a private network. Data protection in transit is the protection of this data while it’s traveling from network to network or being transferred from a local storage device to a cloud storage device – wherever data is moving, effective data protection measures for in transit data are critical as data is often considered less secure while in motion. In order to achieve this client-server needs to perform and implement,
In this module, Authentication done with public key algorithms (RSA, ECC etc.)

