CaseStudy Banking Regulator
Banking Regulator Implements JISA’s Tokenisation, Encryption and Hardware Security Module for Data Lake Project
The Organisation
The organisation is India’s Banking Regulator under the jurisdiction of Ministry of Finance, Government of India. It is responsible for the issue and supply of the Indian rupee and the regulation of the Indian banking system. It also manages the country’s main payment systems. Until the Monetary Policy Committee was established in 2016, it also had full control over monetary policy in India. It commenced its operations on 1 April 1935. The original share capital was divided into shares of 100 each fully paid. It is a member bank of the Asian Clearing Union. The bank is also active in promoting financial inclusion policy and is a leading member of the Alliance for Financial Inclusion (AFI).
The Business Challenge
The banking regulator has to collect and store personal and sensitive data in a large amount. The sensitive data includes Customer data (Name, Mobile Number, email, Aadhaar Number, PAN number, etc.), Payment sensitive data (customer and beneficiary account details); Payment Credentials (OTP, PIN, Passwords, etc.) and Transaction data was stored in a Data Lake. Data lake is a storage repository which stores large amount of structured, semi-structured, and unstructured data. It stores every type of data in its native format with no fixed limits on account size or file. It offers high data quantity to increase analytic performance and native integration. Just like in a lake it has multiple tributaries coming in, a data lake has structured data, unstructured data, logs etc.
This data would be collected and stored in their system in plain text format i.e. in unencrypted format. If any unauthorized person accesses the data or there is data loss, it would lead a serious data breach. This not only risks harm to the individuals but also strict penalties.
Apart from storing the sensitive data, banking regulation often need to transfer data to and from banks, financial institutions etc. This data also needed to be transferred in an encrypted manner to avoid unauthorized access, data loss etc.
Hence the organisation wanted to store and transfer the sensitive data in an encrypted format. Considering large amount of encrypted data, key management is essential part of the encryption solution.
The Solution
Since the large amount of data was stored in unstructured format, appropriate solution needed for securing each kind of data. Considering this challenge, JISA has deployed encryption and tokenization solutions for the organisation.
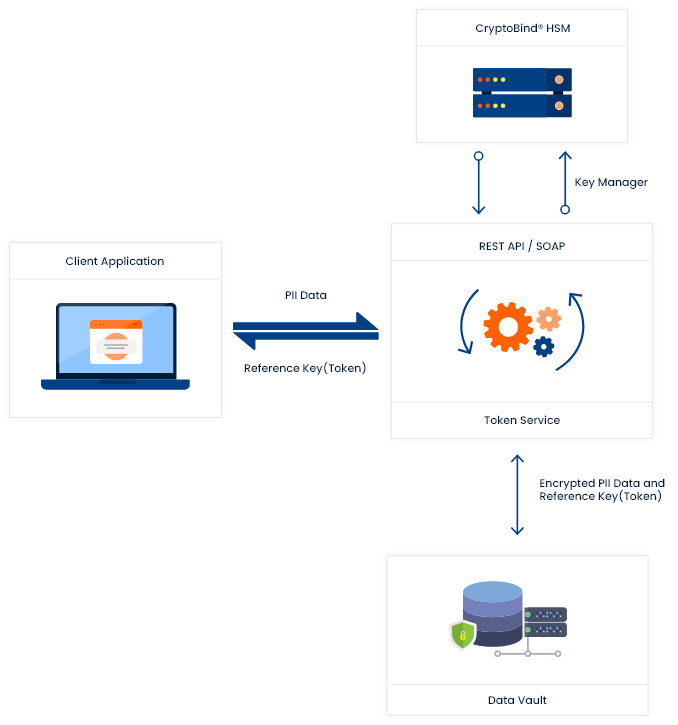
JISA’s CryptoBind SecureVault (J-Vault Vaultbased Tokenisation) was deployed primarily to store PII data, financial data. CryptoBind SecureVault allows applications to tokenize and replace sensitive data with token values. In order to secure sensitive data, JISA has developed this solution that will help agency to implement an encrypted secure Data Vault to tokenise and securely store PII data.
It exposes SOAP/ REST API to directly and securely store the data in a Data Vault using the Tokenization method. CryptoBind SecureVault is connected to CryptoBind HSM (Network Security Module by JISA powered by LiquidSecurity) to manage encryption keys.
ADV Admin Portal is hosted on client location which works in sync with tokenization engine services. It facilitates various operations like User Access Control and Management, Application Onboarding, Key Management, Token Management and Policy Management.
CryptoBind SecureVault Deployment Architecture:
CryptoBind HSM (Network Security Module by JISA powered by LiquidSecurity) is a high performance hardware based transaction security solution for cloud data centers, Enterprise, government organisation and ecommerce applications. HSM family provides a FIPS 140-2 level 3 certified solution that provides elastic and centralized key management and key operation functionality. As required by organization, encryption keys are securely stored in CryptoBind HSM.
To add an additional layer of security CryptoBind Transparent Encryption (J-STE Transparent Data Encryption) was implemented to encrypt data files at rest. Data at rest is subject to threats from hackers and other malicious threats. To prevent this data from being accessed, modified or stolen, JISA’s TDE employ security protection measures such as password protection, data encryption, or a combination of both to encrypt data at rest. The TDE solution is connected to CryptoBind HSM to manage TDE encryption keys. By implementing CryptoBind Transparent Encryption, if a hacker or malicious user tries to access data files, his access is blocked by encrypted files.
CryptoBind Transparent Encryption Deployment Architecture:

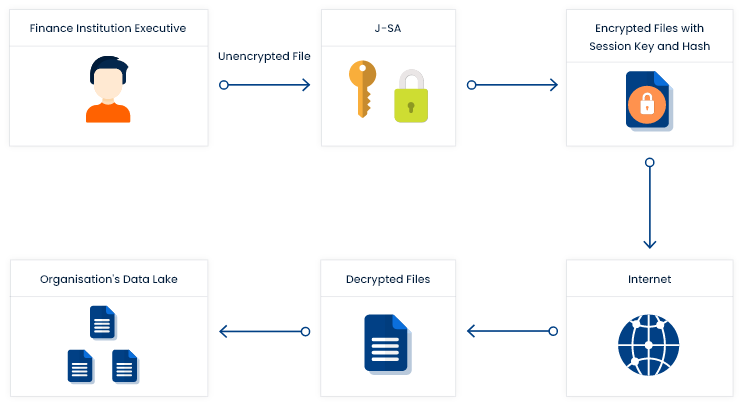
To transfer the sensitive data to and from banking institutions or financial institution, CryptoBind SecureApp (J-SA Data in Transit Encryption) has been deployed. JISA’s CryptoBind SecureApp provides encryption of data in transit. Data in transit, or data in motion, is data actively moving from one location to another such as across the internet or through a private network. JISA’s CryptoBind SecureApp involves a lightweight library which works seamlessly in desktop, enterprise, and cloud environments as well.
CryptoBind SecureApp Deployment Architecture:
The Result
Compliance with Data Protection Regulations
With the help of this solution organisation’s system is complying with data protection act and regulations.
Reduce risk of data breach
Tokenization replace sensitive PII data with random string i.e. ‘Token’ which has no meaningful value. Even if a hacker tries to access this token, he cannot access sensitive data. This in turn reduces risk of data breach.
Secure Data Transfer
End-to-end encryption can ensure that data is protected when users communicate. It also protects data and credentials as they pass over a network.
Ease of Implementation
Due to RESTful APIs, the solution can be swiftly integrated with existing products. JISA’s solution implements Format Preserving Encryption which preserves data format and compatibility with existing applications and database schemas. With RESTful API, PKCS# library, it is easy to ass standards-based secure key management and data encryption services to customized data security solutions
FIPS Compliant Protection
Encryption/ decryption keys are protected by FIPS compliant device and restricting direct access to the keys.
Audit Trails
Audit trails are securely stored for non-repudiation. Full auditing of all user access and client application operations
Alerts
JISA’s implemented solution is able to provide unauthorized access alerts.
About JISA
JISA is a young Information Technology company providing various Authentication products and Solutions.
All our Public Key Infrastructure(PKI) & Cryptographic solutions are sold under brand name CryptoBind®. With strong core competencies in Cryptography and PKI, JISA offers solutions built around Public Key Infrastructure (PKI), the framework that brings confidentiality, authentication, privacy, and non-repudiation.
“JISA has an entire range of software applications based on cryptographic algorithms and protocols”