Introduction
This Use Case has been developed for JISA’s CryptoBind HSM (Network Security Module by JISA Powered by LiquidSecurity) product. JISA’s HSM can be used for PKI deployment.
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email.
Why to use CryptoBind HSM in this use case?
PKI consist of protocols, services, and standards supporting applications of public key cryptography. PKI manages cryptographic keys, digital credentials, enables the establishment of trust relationships in an extended enterprise environment. HSM is a dedicated cryptographic component, located on the network or connected directly to a dedicated server, which is used as a basis for building an enterprise PKI infrastructure to securely manage cryptographic keys and digital certificates.
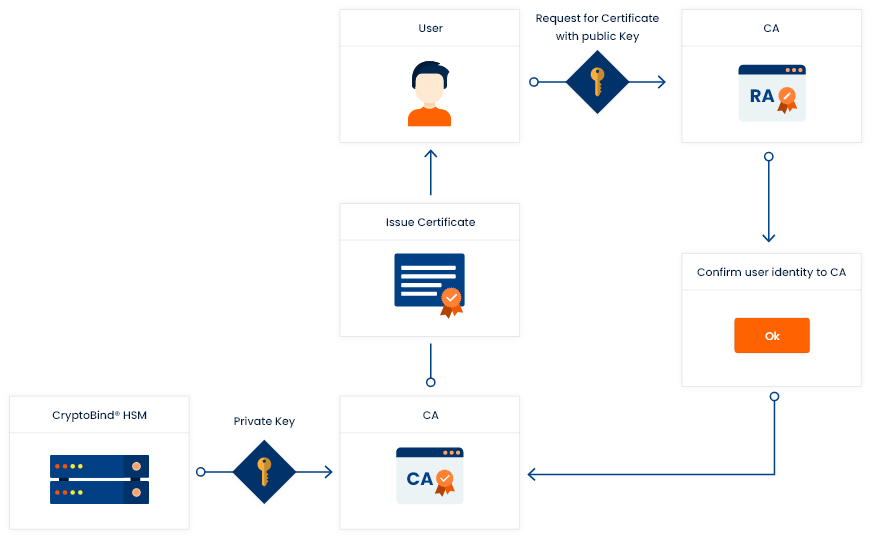
Use case flow
PKI consist of key components viz Digital certificates, certificate authority, registration authority and HSM. These elements on a secure framework i.e. Public Key Infrastructure can protect the identities involved as well as the private Information used in situations where digital security is necessary, such as smart card logins, SSL signatures, encrypted documents CA etc.
A user applies for a certificate with his public key at a registration authority (RA). The RA later confirms the user’s identity to the certification authority (CA). CA issues the certificate signed with the private key. The user can then use this certificate to prove his identity.